- Services
- Industries
- Automotive
- Battery
- Building inspection
- Fire alarms system testing
- Household appliances
- Installation materials
- Industrial machinery
- IT & audio video
- Laboratory, test & measurement
- Lighting equipment
- Maritime, oil & gas
- Medical & healthcare equipment
- Military & aerospace product testing
- Wireless & telecom
- Resources
- About
- Blog
- Events
You don't know how secure your system is before someone tries to break in.
Your home is your castle - Think of your IT system as your building
Not only does your building have hundreds of possible entrances and dozens of access systems – they are also constantly being changed, updated – and outdated.
In this building, you store all your information – both of your customers and what you need to run your business, including sensitive information about your colleagues. This means no one should be given access to the building without authorisation. How can you prevent that? How do you establish confidence that your doors, entrances, and windows are secure?
Having an external company perform a vulnerability scan, a penetration test or both of your IT systems is a cost-effective solution that considerably increases security for your company, your colleagues, and your customer's data.
There is clear evidence that regular vulnerability scans and penetration tests make companies more robust against cyber-attacks and make it harder for an attacker to get further into the network.
Vulnerability scanning
Using a building as an example, a vulnerability scan would be to check all access points and security functions of the building. A vulnerability scan of an IT system will check for insecure settings and configurations, out-of-date software, etc. However, it does not simulate an actual attempt to sneak or break into your system. Vulnerability scans can be used as services performed regularly as a part of a company security program, or they can be used as the basis for penetration testing.
Vulnerability scans are performed by Nemko using digital tools and can be done remotely. It is a quick and reasonably priced service which requires minimum management attention and provides an improved level of confidence in the security of your network. Conducted regularly, vulnerability scans contribute to more robust outer defences.
Breaking in: Penetration testing
Now, we are breaking into the building! Penetration testing is often referred to as 'ethical hacking' or 'white-hat hacking'. Performing a penetration test (pen test) on a system or software means simulating an attack by trying to access the system like a hacker would.
When Nemko performs a penetration test, we try to enter your system and/or steal information being transferred by the system to test how easy or difficult it is – and hereby identify the vulnerabilities. We sum up our findings in a report which also includes identified improvement opportunities. Penetration testing would require the consent of the system owner.
Why is penetration testing important?
A penetration test provides confidence that updated knowledge is applied by trained and certified subject matter experts to identify weaknesses so you can take appropriate action to protect yourself and your assets. It does not guarantee that a cyber incident will not hit you.
However, it provides you with an overview of the security status of your systems and network and allows you to take action to reduce the identified risk substantially.
Why not use internal staff?
Own staff is the most crucial part of keeping your network secure, but there are two main reasons to use external.
- External pen-testers do not have a thousand "other things to do". They are pen-testers - that's what they do! This means that they have the updated tools, certifications, and competence,
- They also have scheduled the time so the tests will be performed according to plan and not pushed back due to other tasks.
Relevant for small businesses?
It is tempting to think that cyber-attacks only hit large businesses, but statistics say it is not. According to Forbes, 43% of cyberattacks target small businesses in 2022. From the same source, only 14% of these companies have proper defences. And 83% aren't financially prepared to recover from such attacks.
But – what is needed for a small company will differ from the need of a large company, making the service and cost proportional to size. Even a tier 0 scan will help your small company improve security and get an inventory of what software is being used on your servers.
For a first-time scan for a small business, we highly recommend a tier 1 scan. This is because you will get assistance from one of our consultants to prioritize the tasks, answer any questions about the findings, and plan the path.
Not more than you need – the four levels.
The exact need for vulnerability scan/penetration testing varies from company to company, so to make it easier to define, Nemko has developed a service delivery model where each "tier" of service delivery is progressively more advanced and thorough.
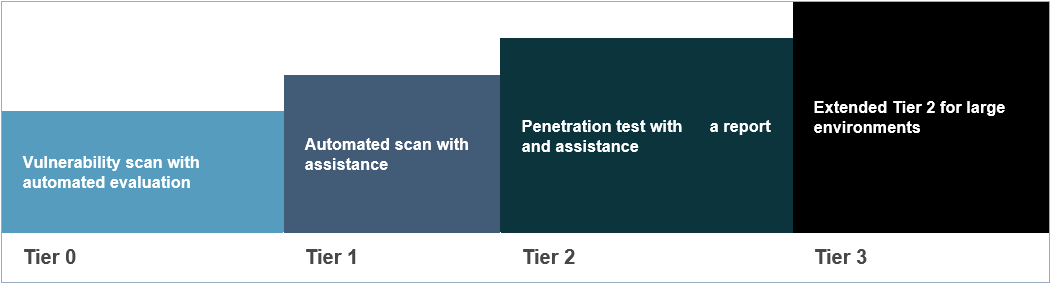
Each tier includes and builds on all lower tiers. For example, if you choose tier 2, tiers 0 and 1 are included in the "package."
Tier 0
The penetration tester conducts a vulnerability scan and provides the customer with an automated report of the findings.
Tier 1
The penetration tester will assist the customer with highlighting and prioritizing the various risks accompanying the vulnerabilities and provide general mitigation strategies.
Tier 2
After performing a vulnerability scan, the penetration tester will perform a penetration test and produce a report with findings and suggestions for remediation.
Tier 3
This is an extended version of Tier 2. This applies to projects where additional time is needed due to the scale and complexity of the penetration test.
One-offs or subscription services
Regular scans are recommended because changes frequently happen in an IT system, and new vulnerabilities are discovered in existing programs. A typical solution is running vulnerability scans and penetration testing followed by automated vulnerability scans regularly, e.g., quarterly.
Extensive penetration testing is usually performed as a one-off or at annual intervals.
A typical process
• Defining the scope together with the customer.
• Performing vulnerability scan of the system.
• Using the results from the scan to explore vulnerabilities.
• Present the analysis and recommendations in a report to the customer.
Typically, an automated scan is done periodically, giving the customer a continuous overview of the network.
Nemko can help you close the weaknesses
Our team of cyber security experts can advise you on how to close the weaknesses in your systems by simulating a hacker attack and exploiting any vulnerabilities they come across to get an in-depth analysis of your system's security. This can be done from the inside or as an attempt to get in. It can be performed once or on a regular basis.
We offer penetration testing on networks and can provide vulnerability scanning of networks, Android and iOS applications.
Want to learn more about penetration testing and how it could help your company? Schedule a complimentary call with us at your convenience.
Other network safety services Nemko can support you on
Vulnerability scan
An automated vulnerability scan checks for insecure settings and configurations, out of date software etc. but does not simulate an actual hacker attack (as a penetration test does). Vulnerability scans are therefore cheaper to do than penetration testing. It can be performed on servers and, Android and iOS applications.
This is a quick and cost-efficient way to test and increase the security of your servers.
Hardening
Hardening is to reduce the vulnerabilities of a system by making it harder for an attacker to gain access. The principle behind hardening is to reduce the attack surface and therefor eliminating possible entryways for attackers. This can be done by patching vulnerabilities and making sure everything is configured correctly.
We can assist in checking that CIS (Center for Internet Security) guidelines have been followed.
Hardening can be performed in connection with a vulnerability scan.
Security evaluation
Nemko can also perform security evaluations, which provides you with suggestions on how to improve the security of software and system.
Which network safety service is best for your company?
Frequent vulnerability scans are essential for your business to stay secure. As new vulnerabilities are found every day, a vulnerability scan should be conducted regularly and more frequently than a pen test. They should be conducted at least quarterly, and after any significant change. A vulnerability scan does not actively patch vulnerabilities, but generates a report on the vulnerabilities that are detected.
Hardening and verification of hardening settings can be included in a vulnerability scan. This is a quicker and cheaper way to increase the security of your systems than a penetration test. However, hardening and vulnerability scans are not as in-depth as a pen test, and may not produce the same level of results.
Pen testing is the most in-depth approach to securing your systems and it is therefore more effective than a vulnerability scan but it takes more time and has a higher cost. A pen test should be conducted annually.

Uncover critical security risks before hackers do: watch the on-demand webinar, and get an introduction to penetration testing
On-demand webinar
Our experts will provide practical insights and guidance on how to assess and strengthen your security posture, reduce the risk of a security incident, and protect your company's reputation.
Watch the webinar


